Did you know? 43% of small businesses suffer cyber attacks annually. Some major Cloud security concerns are leakage and data loss (69%), data privacy (66%), and accidental exposure of credentials (44%). It clearly shows how data breaches become one of the biggest concerns for businesses and why they should focus on increasing security measures to protect their data.
This is where Cloud security comes in as a top-notch solution. It allows businesses to add layers of protection on their sensitive information to protect from unauthorized access.
The global Cloud computing market will be valued at USD 1873.59 billion by the end of 2032. The statistics clearly show the growing Cloud security demand. As per the Gartner survey, 80% of businesses plan to increase their investment in cloud security.
Since organizations of all sizes are investing in the Cloud, the need for robust Cloud security is evolving rapidly. So, if you’re experiencing some security issues, you must know the top Cloud security practices you need to implement during the software development. Here, we’ve listed the top ten cloud security practices that you need to implement for high-end security and protection from cyber-attacks. Let’s find out!
Table of Contents
ToggleCloud Security: Overview
Cloud security refers to several practices and strategies designed and developed to safeguard applications and sensitive data. Similar to cybercrime, Cloud security crime is at its peak; thus, designing different Cloud strategies for businesses is important to minimize potential risk factors. Cloud security includes technologies, protocols, and other controls developed and deployed to safeguard important information and applications hosted in the Cloud software. Since Cloud computing deals with running apps and storing a huge bulk of data on remote servers, the chances of data breaching are extremely high.
Generally, these software are managed by Cloud providers like Microsoft Azure, AWS, Google Cloud Platform, and others. Further, all risks are analyzed, and providers suggest different application-based and network security controls for Cloud infrastructure. Cloud security or Cloud computing security is a vast collection of safety measures developed to safeguard Cloud-based applications and infrastructure.
How Does Cloud Security Work?
Cloud security includes protecting your online data, infrastructure, and applications in Cloud computing environments from theft, deletion, and leakage. Cloud security majorly focuses on implementing processes, technologies, and policies together to provide maximum data protection and complete control over privacy. Cloud developers rely on encryption mechanisms as a security measure, whereas customers implement client-side encryption for additional data safety. This limits the attacker’s movement and isolates workloads within the Cloud environment.
Importance Of Robust Software Development Practices
Safe and secure software development will take center stage. Implementing effective security software development practices is important to reduce the increasing cybercrime. According to a report, cybercrime expenses were around $6 trillion till the last few years. However, the number is expected to increase to $10.5 trillion by 2025. Any security breaches drastically impact your business. It not only tarnishes your business reputation but results in monetary losses. Therefore, implementing software development security best practices becomes vital.
Top 10 Cloud Security Practices For Software Development
Here are the 10 best practices for cloud security for software development:
1. Implementing Robust Access Control
When it comes to custom software development, implementing strong control access is important for secure software development. Developers can use strict rules and multi-factor authentication to keep all unauthorized users away. Through role-based access control or RBAC, people can access limited information necessary for their jobs. This reduces the chances of data breaches and minimizes risk factors. Further regular scans and safety controls are implemented to promote tight security.
2. Adopting Zero-trust Architecture
When it comes to software development and security practices, you cannot trust anyone within or outside the organization. Thus, it’s high time to adopt zero-trust architecture. This means you will need to verify everything that wants to connect with your system to ensure there is no room for mistakes. This approach is especially for the Cloud era as all sensitive information about the company is stored on Cloud software. Limited access and strict guidelines to enter your space are the way to go and to deal with all threats.
3. Continuous Security Patching
The best way to keep all threats away is to keep your software updated. Although most people already follow this practice, you cannot put enough emphasis on regular security patching as a popular Cloud security practice. When you keep track of all hardware and software, it manages regular updates, minimizing chances of security risks.
4. Safe Coding Practices
Another important Cloud security practice for a secure software development lifecycle is writing safe and clean codes. Writing code safety is important to minimize the chances of security risks and avoid all errors. If not implemented, these errors may result in vulnerabilities such as SQL injection. Therefore, secure coding is important! Developers can regularly review these codes to minimize security challenges, resulting in smooth business operations.
5. Third-party Risk Assessment
When using Cloud computing, you frequently depend on third parties to complete essential business tasks. Establish a procedure for evaluating risks when choosing vendors, with an emphasis on security procedures, certifications, and data controls. Establish the duties and obligations related to security in provider contracts and keep a close eye on their Cloud environments.
6. Promoting Data Encryption
Encrypting stored and transit information is important to keep the data safe. This is majorly important for healthcare companies where protecting patients’ personal information is a hectic task. Through data encryption, an extra security layer is added, which diffuses cyber attacks and minimizes potential risk factors.
7. Using Threat Intelligence
Another vital Cloud security practice to implement for software development is understanding the potential threats. When you incorporate threat intelligence, it prepares you for future threats and minimizes the chances of attacks. When you work with external intelligence sources, it opens doors, allowing you to view threats from a wider perspective. Using threat intelligence within security systems promotes proactive defense.
8. IAM Utilization
IAM systems control access to certain resources. This is particularly important for industries like banking, where safe identity management is essential. They guarantee that access adheres to the “least privilege” principle and impose strict authentication. It’s critical to update IAM policies frequently to address emerging dangers. A comprehensive view of security and user behavior is provided by connecting IAM with other security solutions.
9. Regular Logging And Monitoring
Continuous monitoring system activities are the most important for detecting any potential security breaches, especially for businesses related to software development and digital transformation. If your business is growing digitally, you must combine logging with alert systems and real-time analysis.
10. Disaster Recovery
We live in a high-tech world where the chances of data breaches always exist. Therefore, you must remain prepared for any security problems as they may arise anywhere and anytime. It is best to have a backup plan to restore lost data, especially in the healthcare sector, where you cannot compromise a patient’s privacy. The business must be involved in continuous planning to recover all losses, safeguard the company’s reputation, and reduce downtime.
Top Five Benefits of Implementing Cloud Secure Practices
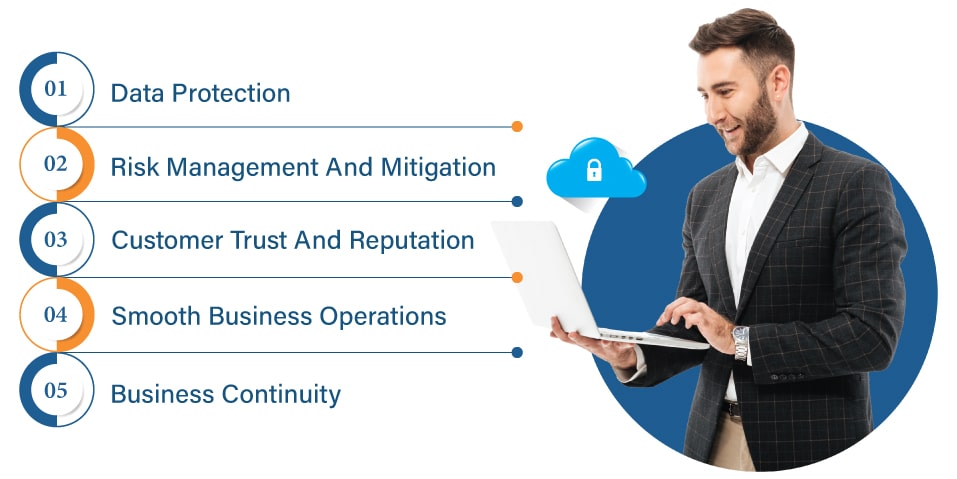
1. Data Protection
Safe and secure practices in the Cloud software safeguard sensitive information from disclosure, unauthorized access, and interception. By implementing data masking techniques and encryption, organizations keep the data confidential, protecting it from unauthorized access.
2. Risk Management And Mitigation
Cloud security best practices assist enterprises in recognizing and reducing security threats related to Cloud computing. Organizations can reduce the frequency and impact of security breaches by managing security risks proactively. Additionally, they minimize vulnerabilities and successfully respond to security incidents through security controls and effective risk assessments.
3. Customer Trust And Reputation
Cloud security procedures enhance client trust and confidence in the company’s ability to safeguard their privacy and data. Organizations may establish a solid reputation for security expertise, draw clients, and set themselves apart from rivals in the market by prioritizing security, putting in place industry-leading security procedures, and displaying a dedication to protecting customer information.
4. Smooth Business Operations
Another major benefit is smooth business operations wherein all possible vulnerabilities are identified at an early stage, reducing disruptions in everyday functioning. This safeguards business reputation and promotes smooth operations.
5. Business Continuity
By guaranteeing the accessibility and dependability of Cloud services and data, secure procedures help to promote business continuity and resilience. Through the utilization of redundancy, failover mechanisms, and disaster recovery solutions, entities can reduce downtime, lessen the consequences of service interruptions, and sustain business activities in the event of an infrastructure failure or security breach.
Cloud Security Software Development Challenges
Cloud security has different challenges experienced by software development firms when they head to the Cloud. Here are some common Cloud security challenges experienced by developers while addressing Cloud security:
1. Data Security And Privacy
One major Cloud security challenge experienced by software developers is ensuring the security of sensitive information stored in the Cloud software. Unauthorized access to data and data breaches are common concerns in Cloud software. Therefore, developers need to access control and implement strong encryption to avoid data manipulation and unauthorized access.
2. Security Monitoring And Incident Response
To quickly identify and address threats, Cloud systems must be monitored for anomalies, unauthorized activity, and security risks. Effective security monitoring and incident response features in Cloud-based applications present challenges for software developers. These challenges include determining pertinent security events, examining audit trails and logs, and coordinating incident response actions among dispersed Cloud resources.
3. Integration And Interoperability
Another major Cloud security challenge is integration and interoperability. Integrating Cloud-based apps with third-party services and on-premises systems increases the chances of security risks. Some common risks are data exposure, API vulnerabilities, and data integrity. Here, the software developers must implement encryption for data in transit, strong authentication mechanisms, and safe APIs for safe integration and interoperability.
5 Factors To Consider To Find The Best Software Development Company
1. Experience And Expertise
While hunting for software development companies in USA, look for the one with relevant experience and expertise that aligns with your project needs. Closely look at their portfolio to understand past work. You may also connect with clients to learn about the developer’s work and behavior.
2. Technical Understanding
Having technical knowledge is an important factor that you must consider when choosing a software development company. Closely evaluate the team’s qualifications and skills to ensure they can handle the project well or not. Based on past projects, you must analyze the developer’s proficiency in frameworks, programming languages, and other technologies.
3. Communication And Collaboration
Effective collaboration and communication are the key to successful project completion. Check if the developers are responsive and follow communication routes often. Additionally, check if they are willing to collaborate with different teams seamlessly to get the best solutions. Choosing a company that follows a simplified channel and maintains open communication.
4. Quality Assurance And Testing
When hunting for the right software development company, choose the one that conducts regular testing for quality assurance. This is important to ensure that the software performs to meet all quality standards. Choose a company that follows a rigorous testing process and suggest the best solutions.
5. Maintenance And Support
Consider the software development company’s scalability and support choices once the project is completed. As your company expands and changes, evaluate its ability to scale resources and enable continuous software maintenance, updates, and enhancements.
Are You Looking for a Tailored Business Software Solution?
Our experts can fulfill your specific needs
How Can DreamSoft4u Help You Build Secured Software?
DreamSoft4u is a globally renowned software development company offering software development services with 20+ years of hands-on experience. Known for crafting compelling solutions, the company delivers robust Cloud security services to small and large enterprises. We have a team of experienced professionals who understand the problem and suggest tailored solutions at the earliest possible. So what’s the wait for? Visit DreamSoft4u today!
Wrapping Up!
Cloud solutions are adopted by several industries worldwide. Still, security issues prevail as it deals with sensitive data; therefore, vulnerabilities and threats constantly evolve. By establishing the best Cloud security practices for software development, companies can protect data, applications, and infrastructure in Cloud computing environments. Although there are several challenges that software developers need to address, incorporating Cloud security practices minimizes risk factors. To safeguard your data on the Cloud software, you must hire a renowned software development company whose experience and expertise align with your project requirements. DreamSoft4u is a leading software development company delivering excellent IT and Cloud solutions for the best results.
FAQs
1. What are some future trends within Cloud security technology?
The Cloud security market is evolving rapidly, especially after the advent of new technologies. Thus, certain future trends like AI and machine learning, quantum computing, blockchain tech, edge computing, and zero trust security models. Besides these, several other future trends may arise for robust security.
2. Why are regular security audits and monitoring important?
Cloud software is prone to security risks and data breaches. Therefore, conducting security audits and monitoring at regular intervals is important. This helps to mitigate potential risk factors and analyze any complexities. It is suggested that audits be conducted within 6 to 8 months.
3. Mention some common Cloud security mistakes that companies make
When it comes to Cloud security, companies often make mistakes. Some common mistakes are not implementing limits to access the company’s sensitive information, not following the company’s rules, and skipping security checks at regular intervals. Another major miss by companies is not providing adequate training to employees.
4. Mention the top tips for data encryption in the Cloud
For data encryption in the Cloud, encrypt transferred and stored data using robust protocols like TLS and AES. Manage encryption keys well with continuous changes, secure storage, and strong creation methods.
5. How do you choose the best software development company for cloud security?
When choosing the best software development company, consider security, scalability, cost, technical skills, certifications and standards, reliability and performance, API integration, and more.



















