The trend and the surge in the software development industry often result in cyber theft, data breaches, attacks, and other cybersecurity risk factors, giving rise to Software development security. According to a report, in the first quarter of 2023, around 6 million data records were breached worldwide, which caused a loss of more than a hundred million. As a result, the need for software development security becomes vital. Another report says over 70% of organizations globally have introduced some kind of security setup.
More than 75% of businesses rely on machine learning and artificial intelligence to mitigate risk factors and find solutions. These statistics prove that it’s high time businesses identify these security challenges and battle against them to protect their applications from attacks. This article is a complete guide to software development security challenges in modern software development. Let’s dive in!
Table of Contents
ToggleImportance Of Software Development Security In Software Development
In the world of software development, software development security is vital as it ensures that your software remains consistent and protected from all attacks. Modern software development solutions need secure software to protect the client’s data. Software development security is fundamental to modern software development as it protects against unapproved access, data breaches, and other harmful activities that can hamper the data.
Above all, with the introduction of distributed computing, cell phones, and IoT, software development life cycle security is becoming more critical. Since all the data is stored on servers that are linked to physical devices, the chances of security breaches exist. As per a report by Infosys, on average, most businesses worldwide make an average investment of $2 million every year on application security and software security. This signifies the importance of software development security in software development.
Potential Cyber Threats And Impacts On Software Development Security
Here are the top potential cyber threats and impacts on software development security:
1. Phishing
Phishing is a cybersecurity or social engineering attack where the attackers can access individual information such as usernames, account numbers, passwords, and other personal data. Phishing attacks can also lead to credit card fraud, data breaches, huge financial losses, and more, generally occurring by clicking on harmful links or downloading unknown files.
2. Malware
Malware, also called malicious software, is a widespread software development security threat that can harm your network, computer, or personal data in the PC or other applications. Malware generally ranges from impacting your computer’s speed and overall performance to stealing personal information and financial data.
3. Cross-site Scripting
Cross-site scripting, also known as XXS, is a computer security vulnerability where attackers can inject malicious codes into websites and applications. Since these vulnerabilities are a prime concern for web developers, attackers can exploit them differently. The severity of the threat is determined by the kind of malicious code infected. Generally, attackers inject client-side scripts to steal important information.
4. Buffer Overflow Attacks
When malicious attackers send huge amounts of data or data bundles into online administrations or applications, buffer overflow attacks occur. It can result in the loss of important information, execution of unauthorized software, or administration interruptions.
5. Social Engineering
Social engineering is another popular kind of cyber threat and impacts security for software development, including malicious actors using misdirection and manipulation to access sensitive information. If they are successful, they can steal the data, disrupting the software development.
8 Most Common Software Development Security Risks
Here are some of the most common software development security challenges:
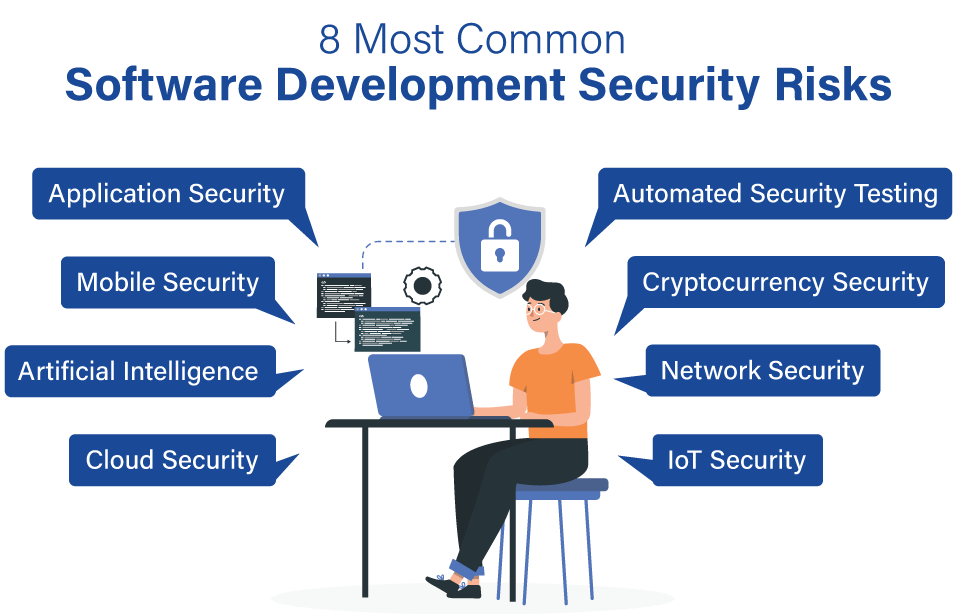
1. Application Security
Application security is a common and fast-evolving software development challenge, as malicious actors continuously attack vulnerable software. To avoid application security challenges, all software development companies make sure that their applications feature robust security mechanisms to provide maximum protection and shield user data against all external threats.
2. Mobile Security
Since custom organization software development and enterprises are choosing mobile-based platforms, mobile security is evolving as a prime security concern for software developers around the globe.
3. Artificial Intelligence
Artificial intelligence is the newest technology, experiencing all the hype. However, it is a common software development security challenge as it is the responsibility of developers to remain updated with all the latest updates to trace all possible security challenges. All software developers must understand the consequences of AI models and should use strong security features to protect important data from breaches.
4. Cloud Security
In the last decade, cloud-based storage systems have increased significantly. If more enterprises and organizations plan to transfer their applications and data onto the cloud software, cloud security may evolve as a major Software development security challenge. Although it is one of the most protected and trusted ways to store your information, it can offer access to unauthorized sources as well.
5. Automated Security Testing
With all the latest updates and continuous changes, the software is becoming more complex, making it challenging for developers to manually test all applications and their security to determine any malware or security concerns. Several security testing tools in the market allow developers to detect any security challenges and mitigate risk factors before they become a threat and cause destruction.
6. Cryptocurrency security
In the last few years, cryptocurrencies like Bitcoin, Ethereum, and others have become increasingly popular; thus, they have evolved as potential targets for scammers and hackers. All software developers must build strong security measures to eliminate all related risk factors. Developers can use secure frameworks and coding practices like proper authentication and authorization, input validation, encryption, and data storage strategies.
7. Network Security
Network security is a vital aspect of all secure software programs. Developers must be well aware of all potential threats caused by network security. Thus, they must develop a robust software development security application with excellent security measures to protect all sensitive data from attackers.
8. IoT Security
The rise of the Internet of Things or IoT has contributed to the need for solid or robust IoT security and safer applications gadgets. Since more people are migrating to these devices, the security risks are developing. It is the developers’ responsibility to understand all significant security threats and take essential steps to protect all information.
Best Practices To Determine Chances Of Data Breaching
Here are some of the best practices to determine the cases of data breaches:
1. Implement Security Policies
Businesses must establish a well-defined framework of all security procedures and guidelines to reduce the chances of security breaches and safety concerns. Major steps are establishing security guidelines for coding, setting up user access control, relying on security programs for patch management, and continuously updating the system’s security settings.
2. Performing Continuous Security Audits
Another best way to determine the chances of data breaches is by performing continuous security audits. These audits are conducted to examine different aspects of software development security closely. These include code practices, system architecture, policies for accessing users, ways to authenticate users, etc.
3. Rely On The Secure Development Lifecycle
Secure development lifecycle, also known as SDL, is regarded as one of the most trusted ways to ensure software security. The SDL features multiple phases: development, design and testing, integration, and deployment. The software goes through a robust security checking and testing process at every stage, promising system security.
4. Keep An Eye On System Activity
The business must keep a close eye on all its system activities. In case you spot any suspicious activity like other internet traffic, unauthorized user access, and more, you must report it. Regular monitoring keeps the software free from all risk factors.
5. Implement Encryption For Data Storage
Known as one of the best ways to protect your data and sensitive information, encryption tools ensure that only authorized people can access the data. This minimizes the chances of data breaches and reduces risk factors.
Top Security Coding Practices To Avoid Malicious Attacks
Here are the top security coding practices to avoid malicious attacks:
1. Security Logging
Security logging is a widespread practice to avoid malicious attacks. You can outsource a software development company for security implementation to easily track and observe ongoing application events such as alerts, errors, and more. These security logs determine any potentially suspicious activity that can occur within the application.
2. Input Validation
As the name suggests, input validation is a security coding practice that confirms and validates users’ inputs in a particular software application. This makes sure that the data is 100% precise and accurate.
3. Handling Errors And Exception
Handling errors and exceptions is a commonly used security coding practice that identifies and repairs all existing bugs in the application. In case any error occurs, it minimizes the chances of crashing security flaws and clears all errors.
4. Security Testing
When developing modern software, security testing is a crucial coding practice essential to avoid malicious attacks and risk factors. It assists in determining all possible software weaknesses, including programming, deployment, and designing.
How Do You Build Modern And Secure Software?
Here is a step-by-step process to build a feature-rich and secured software:
1. Planning
First and foremost, start by planning the entire Software development security cycle. This helps software developers determine different technologies, understand the project’s scope, and establish a timeline for everything.
2. Create A Requirements Specification
Understand all functional as well as non-functional requirements of your software design.
3. Design UX And UI
Once you have clearly understood the project requirements, it’s time to design UX and UI. Go for an easy-to-use and simplified interface.
4. Security Testing
The next step is testing the software on the grounds of security. This step ensures that your software is 100% free from any vulnerabilities.
5. Security Training
Security training is essential for secure software development. Security training involves educating the team on vulnerabilities, secure coding, threat modeling, and security protocols.
6. Code The Solution
Wrote clean computer codes, maintained technical documentation, designed a complete process flow, and ran thorough tests.
7. Set The Ready Solution Live
Once you have tested the software in real-time under real-world scenarios, it’s time to launch the software. Additionally, provides maintenance and complete support.
You can also hire a software developer who offers excellent software development services for your business.
Why Choose Dreamsoft4U For Software Development?
dreamsoft4U is a globally renowned Custom software development company known for offering tailored solutions that drive seamless results. Here, we deliver customized solutions that meet your business needs perfectly. Additionally, we have a team of highly experienced professionals who use the latest tools and technologies to build strong software.
Some of the major services offered by dreamsoft4U experts are software development, UX/UI services, testing, web development services, cloud services, staff augmentation, and more. Here, experts keep a client-centric approach to offer the best services possible.
Get Your End-to-End Customize Software Solution
Connect with our experts to turn your idea into reality
Frequently Asked Questions
1. List some of the best security coding practices to avoid malicious attacks 300
Here are the top security coding practices to avoid malicious attacks:
- Security Logging is a popular safe coding technique that identifies all suspicious activities.
- Input Validation is a process of validating a user’s input in all software applications.
- Handling errors and exceptions allows for determining and repairing application problems and bugs.
- Secure Authentication and Authorization ensure that only authorized users access the software.
- Security Testing is done to evaluate all pain points and weaknesses.
2. Mention the top advantages of integrating DevOps and security practices
Some major benefits of integrating DevOps and security practices include improved efficiency, reduced cost, security and compliance, trust, quality assurance, and agility.
3. I want to hire a software development firm to develop software for my company. What factors should I consider while hiring?
Some major factors while hiring a software development firm to develop secure software are:
- Years of experience and great expertise
- Necessary technical skills for application development
- A reliable quality assurance system
- Check out the quotation and pricing system
- They must offer excellent custom software development services
- Great communication skills are a must for a smooth development process.
4. What are some potential security challenges in developing modern software?
Some potential security challenges in modern software are application layer attacks, systems layer attacks, database layer attacks, and attacks on network layers. Besides these, other challenges include data theft or loss. Such security challenges arise due to insecure access control systems, insecure programming practices, malicious activities, and more.
5. List some insecure practices while developing software
Some of the most insecure practices you may engage in while developing software are cryptographic failures, including not hiding important information such as payment info, passwords, and personal data. Practices like insecure design, security misconfiguration, infection, insurance coding practices, broken access control, security logging, monitoring failures, and others are other insecure practices while developing software.
Wrapping Up
With the changing technologies and regular updates, the modern software development process has experienced several security risks and challenges. As the complexity keeps increasing, developers are always searching for the best ways to keep their software safe and secure.
This article highlights the top 8 Most Common software development security risks developers experience during their careers. Additionally, we have always jotted down some of the best practices, which helps to get rid of these challenges. Like most organizations in the world, it’s high time you invested in these security solutions and got maximum benefits.